READ MORE: What’s The Latest Thinking About Security? Two Words: Zero Trust (The New Stack)
If you create a virtual machine on any public cloud and expose it to the internet, within 15 to 20 minutes someone will have scanned it, identified it, and taken full control.
No organization can afford to be careless about its security. But cloud architecture makes old ways of keeping systems and data safe obsolete.
The new security methodology is described as “zero trust” in a new eBook from The New Stack, “Trust No One & Automate Everything,” which calls for not only technology that automates authentication and authorization tasks, but also organization-wide cultural changes.
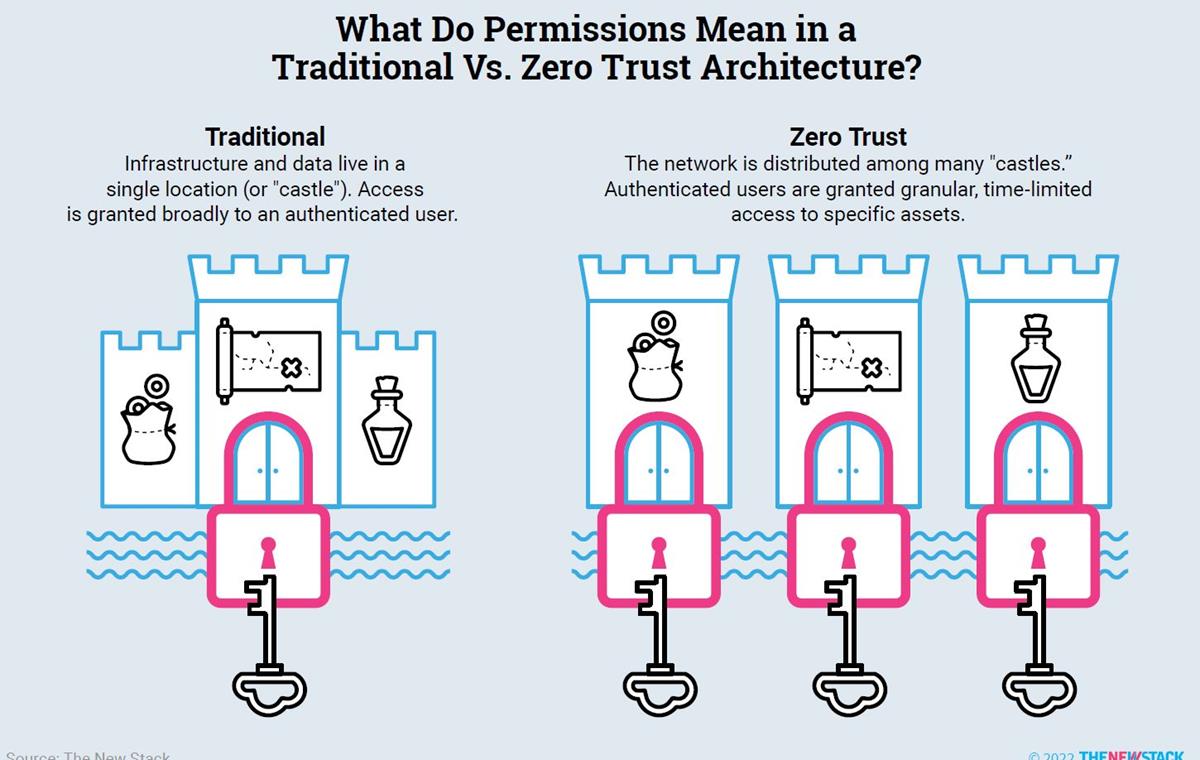
Zero trust involves eliminating the idea of “trusted” anything — no trusted users, no trusted devices.
“Zero trust assumes that the system has broken down completely, so that each individual asset is a fortress of one,” the eBook explains. “Everything is always hostile wilderness, and you operate under the assumptions that you can implicitly trust no one. It’s not an attractive vision for society… because it makes sense to eliminate the human concept of trust in our approach to cybersecurity and treat every user as potentially hostile.”
The core goal of a zero trust policy is data protection.
“If you lost my data, you cannot un-lose it,” says Leonid Belkind, CTO and co-founder of security automation company Torq, which sponsored the report.
The problem is that as more and more parts of a company’s business run on networks in the cloud — rather than being isolated on-premise or in one data center, all the myriad interconnections become increasingly more difficult to protect. It’s harder to ringfence exactly what is “inside” your network versus what is “hostile wilderness.”
“Cybersecurity has to be a part of the organization’s strategy. Zero trust should inform both what is protected and how access is controlled, while security automation helps put those zero trust principles into practice. Together, zero trust practices and automation can also help organizations remediate incidents as quickly as possible and ensure that the initial zero trust architecture remains secure as events happen.”
— Leonid Belkind, Torq
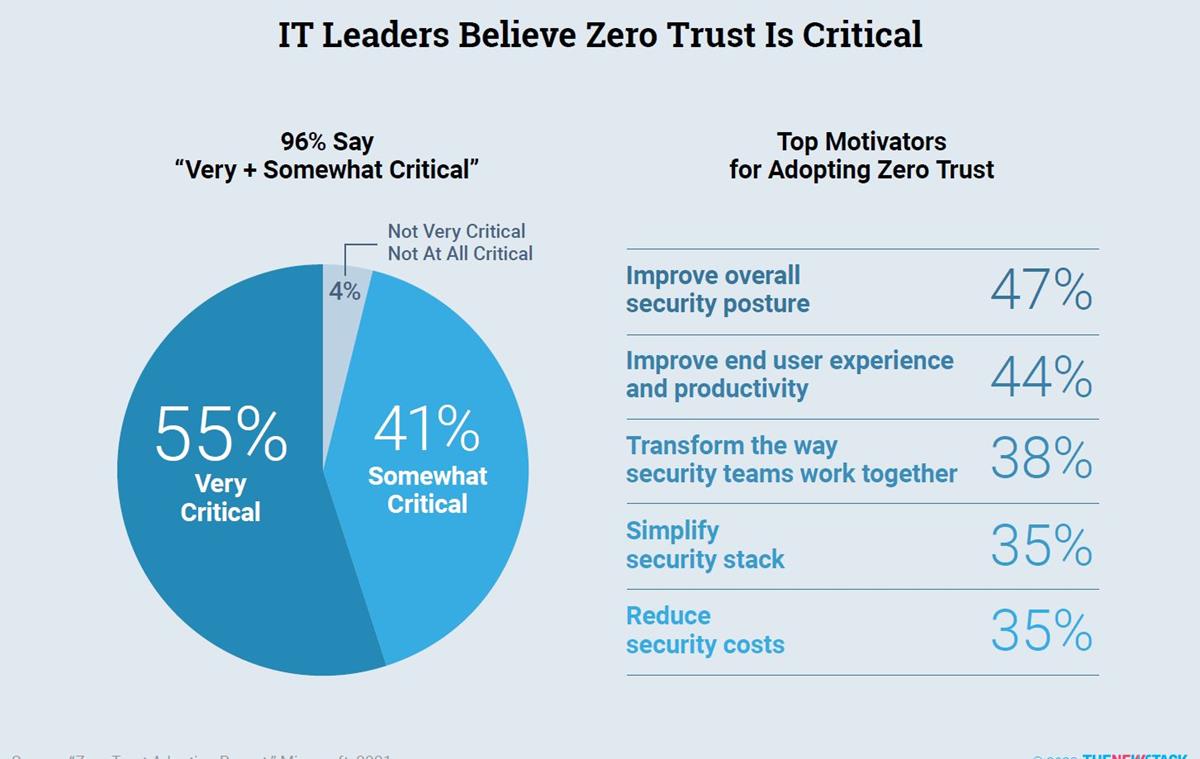
Turns out that the concept of zero trust is close to universal — what CEO wouldn’t want to eliminate any and all risk of a data breach? Yet “vanishingly few” companies are implementing it effectively. Sixty-five percent of companies use shared logins and 42% use shared SSH keys, according to a 2022 survey by strongDM. Both practices run counter to zero trust strategies.
According to Belkind, implementation starts with granular authentication systems, “which means forcing any users, human or server, that want to access a resource to prove that they are who they say they are.”
Once you’ve authenticated a user, the next step is to follow that up with authorization or enforcement: Is that user allowed to perform the action it wants to perform?
Per the report, one of the things that sets zero trust apart is that it requires extreme granularity, allowing users to access or alter only the very specific resource they’ve requested access to, at the specific time they’ve requested that access.
“Authentication simply means proving that the user, whether a human or computer user, is in fact who they claim to be. Authorization means establishing, once we are certain of the user’s identity, that this person or service is permitted to access the resource that it is requesting access to.”
The Role of Automation
There is an assumption that this process must always be hundred percent automated but the report says that’s not true. Clearly, without some automation tools it would be impossible to get anything done in a zero trust system. But some types of requests can, and should, be reviewed manually by a human, it says.
“In fact, for zero trust network access of users, the system could be semi-automated, it could involve people in the loop,” Belkind says. “I don’t necessarily assume that we are talking about machine-to-machine communications.”
EXPLORING ARTIFICIAL INTELLIGENCE:
With nearly half of all media and media tech companies incorporating Artificial Intelligence into their operations or product lines, AI and machine learning tools are rapidly transforming content creation, delivery and consumption. Find out what you need to know with these essential insights curated from the NAB Amplify archives:
- This Will Be Your 2032: Quantum Sensors, AI With Feeling, and Life Beyond Glass
- Learn How Data, AI and Automation Will Shape Your Future
- Where Are We With AI and ML in M&E?
- How Creativity and Data Are a Match Made in Hollywood/Heaven
- How to Process the Difference Between AI and Machine Learning
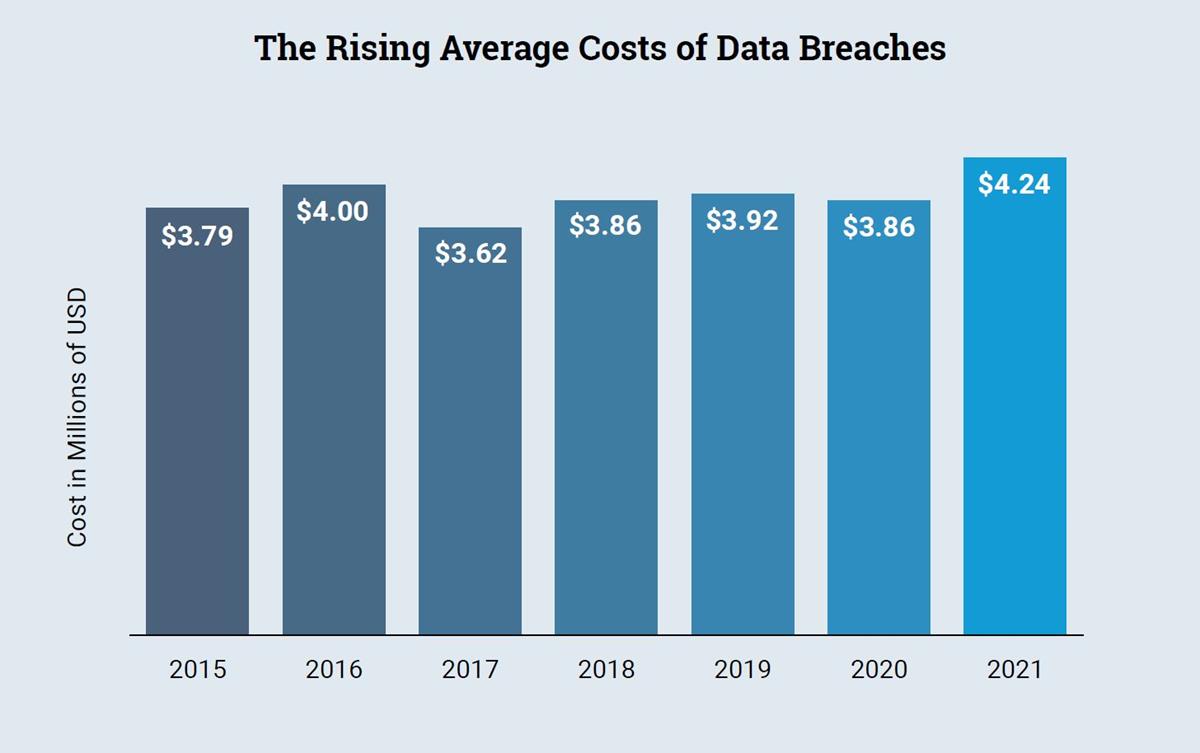
Since the C-suite is likely to continue being held responsible for data breaches, cybersecurity can’t just remain a backwater of the engineering department.
“Cybersecurity has to be a part of the organization’s strategy,” Belkind urges. “Zero trust should inform both what is protected and how access is controlled, while security automation helps put those zero trust principles into practice. Together, zero trust practices and automation can also help organizations remediate incidents as quickly as possible and ensure that the initial zero trust architecture remains secure as events happen.”
READ MORE: What’s The Latest Thinking About Security? Two Words: Zero Trust (The New Stack)